Action :
tom.realm (Category :
tom, Name :
realm, By :
kikonf)
Complete Name :
tom.realm.by.kikonf
Version :
4.0 License :
Modified BSD License
Purpose of the tom category :
Easy to customize. This category use in background the Kikonf Repoz tools to create and configure
Apache Tomcat ®
root installs and
Catalina bases at any level (
server.xml,
hosts or
defaults).
You can use it to manage the whole
Tomcat ® Architecture.
Purpose of this realm plugin : This Action configures a Tomcat Realm.
The following shows in what part of a typical Architecture is likely to be found, the Resource configured by Action : tom.realm
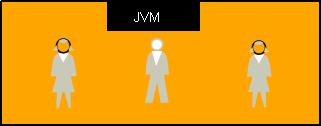

This Action configures a Tomcat Realm.
In the Tomcat scheme, the Realm Name is taken from the <realm-name>
element of the web application's <login-config>. If not set the default is "Authentication required".
1. DEFINITION
A Realm is a store of usernames and passwords that identify valid users of a web application
plus an enumeration of the list of roles associated with each valid user.
2. DECLARATION
a. The Tomcat Administrator configures the store for one of the 6 kinds of Realms provided by tomcat.
b. The Tomcat Administrator tells Tomcat to use this store using the Kikonf Action: realm.
c. The Developpers, into the WebApplication web.xml file :
_ declare the Realm and the Authentification mechanism to use for their Application
using the tag login-config.
e.g.:
<login-config>
<realm-name>BASIC</realm-name>
<auth-method>myrealm</auth-method>
</login-config>
In this sample "myrealm" suppersedes the default Realm Name: Authentication required.
_ declare the Role they need using the tag security-role.
e.g.:
<security-role>
<role-name>manager</role-name>
</security-role>
_ declare the Autorisation level they grant on the Web Application component using the tag ecurity-constraint.
e.g.:
<security-constraint>
<web-resource-collection>
<web-resource-name>private</web-resource-name>
<url-pattern>/private/*</url-pattern>
</web-resource-collection>
<auth-constraint>
<role-name>manager</role-name>
</auth-constraint>
</security-constraint>
3. SAMPLE APPLICATION
Tomcat 5 provide a sample Application using Realm at http://localhost:8080/jsp-examples/security/protected/.
4. The Tomcat Authentification mechanism
This excerpt from the Tomcat official site http://tomcat.apache.org, realm-howto.html explains
how Tomcat deals with Authentification.
When a user attempts to access a protected resource for the first time,
Tomcat 5 will call the authenticate() method of this Realm.
Once a user has been authenticated, the user (and his or her associated roles) are cached within Tomcat for the duration
of the user's login. (For FORM-based authentication, that means until the session times out or is invalidated;
for BASIC authentication, that means until the user closes their browser). The cached user is not saved and restored
across sessions serialisations.

Trademarks :
- "Apache", "Apache Tomcat" and "Tomcat" are trademarks of the Apache Software Foundation.
- "Java" and "JVM" are a registred trademarks of Oracle and/or its affiliates.
- Other names may be trademarks of their respective owners.